“Quantum computing will solve complex problems that would take today’s computers millions of years to solve…
– Matthew D. Ferrante, CISO
conversely, quantum computing will cut through 98% of the world’s cyber defenses like a hot knife through warm butter.”
41,515 Active Engagements
Introduction
Quantum computing is progressing at an impressive rate due to research funding from large companies such as Amazon and Intel. In 2019, Google published a paper confirming that a quantum computer had solved an algorithm faster than the world’s most advanced classical computer. On top of this, Quantum computers have been doubling their functional qubits or computational power each year. While this may be advantageous to the medical field and optimization it creates an entirely new landscape of problems for cyber security. Cybersecurity professionals must stay ahead of new quantum security threats and know what systems are at risk.
Data Scraping
Website data is one such example of a system that could already be vulnerable to the development of quantum computing as hackers employ techniques such as data scraping to collect encrypted data. Governments already take advantage of this concept by downloading and storing data from the internet until they can break the cryptography and access it. There is a much greater threat to long-term data like a secret recipe than more temporary data like credit card information that will be obsolete by the time a quantum computer can decrypt it. The potential of hackers collecting data now that they currently cannot decrypt and waiting for a time when quantum computers will be able to decipher the stolen data is a serious threat. This puts data that requires confidentiality well into the future at a great risk. Banking, government, and business secrets that were assumed to be safe at the time could be revealed in the future causing significant damage to the corresponding institutions. This signifies the fact that if we wait until quantum computers can break encrypted data to take defensive measures it will already be too late. There are solutions to the threat of data scraping as researchers have been working to develop quantum-safe encryption. This will ideally prevent current data from being decrypted by quantum algorithms in the future.
RSA Encryption
Possibly the most significant threat posed is the decryption of the RSA algorithm. RSA is used to secure communications on the internet and by modern standards is impenetrable through brute force. With the emergence of quantum computers this all changes, meaning our communication methods are no longer secure. RSA is an asymmetric public-key cryptosystem that’s extensively used for secure communications. Attacks on RSA consist of factoring an extremely large number that’s the product of two large prime numbers. Attempting to decrypt the RSA algorithm using the world’s fastest supercomputer would take several human lifetimes.
This is where Shor’s algorithm comes in, it takes advantage of the fundamental properties of quantum computing to factor large numbers in a fraction of the time it would take classical computers. Experts estimate that to break RSA encryption with Shor’s algorithm a quantum computer with 20 million physical qubits would be required. With this kind of computing power available it would take Shor’s algorithm about 8 hours to break RSA encryption. Currently, modern quantum computers only have a little over 1,000 qubits however, historically the amount of qubits available has doubled each year leading researchers to believe that 20 million qubits will be achievable in the next 10 -15 years. With this threat quickly approaching many forms of quantum cryptology are being considered as a solution. Some of these methods are Quantum Key Distribution (QDK), quantum coin flipping, position-based quantum cryptography, and device-independent quantum cryptography.
Post Quantum Cryptology
The National Institute of Standards and Technology (NIST) is not idly standing by as this threat emerges. They have begun work on Post-Quantum Cryptology Standardization (PQC). The goal of this in their words is, “to develop cryptographic systems that are secure against both quantum and classical computers, and can interoperate with existing communications protocols and networks.” Once the PQC is finalized in 2024 the United States has passed legislation to put it into effect immediately. Web browsers must also adhere to the PQC starting in 2025 if they wish to operate in the US. A mandated transition to PQC in 2025 to 2033 will occur for all national security systems, making PQC the new standard.
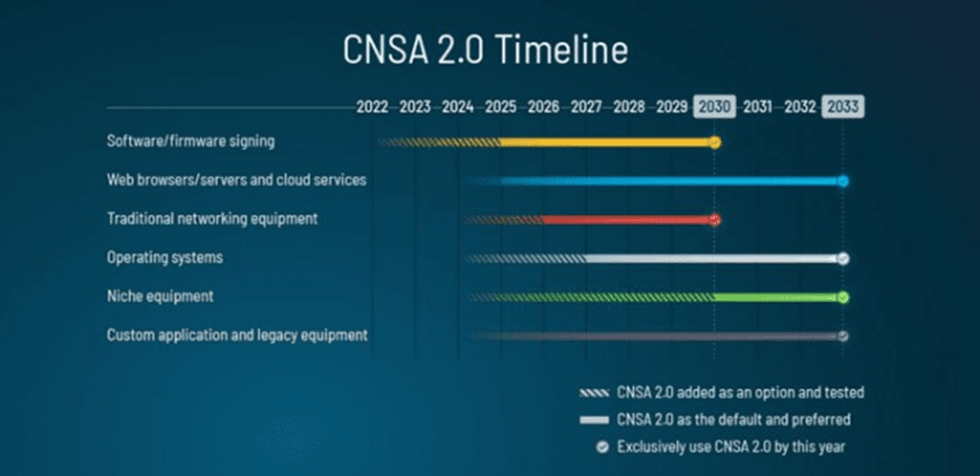
The extensive requirements in this list put substantial pressure on the organizations interacting with the national security agency. Software, cloud services, and operating systems collectively make up a large amount of a company’s information technology, so bringing them up to new standards will be a large commitment. Fortunately, with pressure from the government to have Post-Quantum Cryptology Standardization methods employed, private organizations should follow suit and better protect themselves as well. Before they do, there needs to be better education on Quantum computing and the risks associated with it from a top-down perspective of organizations. Upper management needs to be prepared to allocate resources to protect their organizations from quantum attacks and explain why it’s necessary. Along with training their defense teams on how to properly conduct the implementation of their new defense systems.
Conclusion
With the ever-changing cyber landscape, the best thing organizations and cyber professionals can do is be proactive. It’s essential that organizations understand the change that’s coming and are properly prepared for the expenses that will come with it. Without the proper knowledge and technology companies will be vulnerable to quantum attacks and could pay dearly if systems are compromised. Quantum Computing is a huge threat to the current encryption systems that are in place. However, with proper preventative action, these threats can be nullified before they come to fruition. Proactive programming and defense will always be key to creating a safe cyberspace and protecting sensitive information for years to come.
Ready to transform your business with security by design? Contact Citanex today!
Related Articles
Sources
https://csrc.nist.gov/Projects/post-quantum-cryptography
https://csrc.nist.gov/news/2022/pqc-candidates-to-be-standardized-and-round-4 https://www.encryptionconsulting.com/is-quantum-computing-a-threat-to-cyber-security/
Footnotes
Recent Articles
- Messaging Apps Compared 2025: SMS, iMessage, RCS, Signal, & More
- Understanding Quantum Computing vs. Artificial Intelligence
- Quantum Computing: Friend or Foe to Global Society?
- COMPLACENCY: The Silent Threat – Why It Kills and Why It Matters
- Iran’s Cyber Warfare: Strategies and Global Defense